Microarchitectural Data Sampling (MDS) vulnerability explained
Microarchitectural Information Sampling (MDS) is a CPU side vulnerability. According to Intel, its CPU has some loose points that tin be exploited by hackers. This means taking command of the CPU to be able to read very curt term information stored in CPU internal buffers. Permit's see how it works. We will besides tell me how to find out if your organization is affected from this ZombieLoad exploit.
MDS – Microarchitectural Information Sampling

Mod Intel processors employ data storage in its internal buffers, the data being sent to and from the processor's enshroud. The internal buffers of processors are used to cut compute time. For this saving of processor time, information from processors is start stored in internal memory built into a processor like Intel. The data is of the format: Time, Information, and IF_VALID columns. It is to brand sure if a piece of information is still valid at a given time. This is transferred to CPU cache for use with other firmware or any other software on the estimator.
The microarchitectural data sampling (MDS) vulnerability is a method whereby hackers steal data from processor's ultra-small buffers in real fourth dimension. In each calculator session, data is stored with filters (Time, DATA, IF_VALID) into these mini-caches. They go along changing very fast that by the time it is stolen, its value (validity too) changes. Still, hackers can utilize the data even if the information inside processor filters/memory changes, allowing them to take command of the machine completely. It is not evident. Problems begin when the hacker obtains whatsoever encryption key or any other useful data from the mini buffers in the processor.
To rephrase the above, hackers can collect data fifty-fifty though the life of data stored is extremely short. As said earlier, data keeps on irresolute, and so hackers take to be quick.
Risks from Microarchitectural Information Sampling (MDS)
Microarchitectural Data Sampling (MDS) might give abroad encryption keys and thereby gain command over files and folders. MDS might give away passwords too. If compromised, the computer tin be bricked like in instance of Ransomware.
Malicious actors can excerpt data from other programs and apps once they suspension into the processor retentiveness. Obtaining the RAM information is not difficult once they have the encryption keys. Hackers use maliciously designed web pages or programs to gain access over processor data.
Worst of all is the inability of a compromised calculator, not knowing that it has been compromised. MDS attack won't leave anything in the log and doesn't leave any footprint anywhere on the calculator, or network, and so chances of anyone detecting it are very less.
Types of MDS vulnerabilities
As of at present, 4 variants of the microarchitecture are detected:
- Microarchitectural Load Port Data Sampling
- Microarchitectural Store Buffer Data Sampling
- Microarchitectural Make full Buffer Information Sampling, and
- Microarchitectural Information Sampling Uncacheable Sampling
This was the longest (one year) period for which a vulnerability was found and kept equally a secret until all operating arrangement manufacturers and others could develop a patch for their users.
Some users questioned why tin can't they simply disable hyperthreading to protect against MDS. The reply is the disabling hyperthreading does non provide any kind of protection. Disabling hyperthreading will brand the computers boring. Newer hardware is existence built to counter the possible MDS attacks.
Is your reckoner vulnerable to MDS?
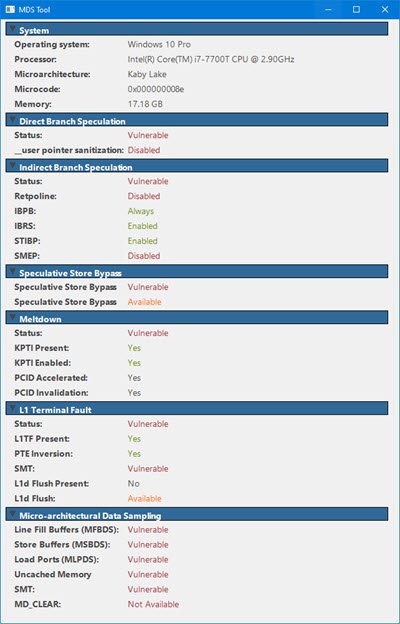
Verify whether your system is vulnerable. Download the MDS Tool from mdsattacks.com. You volition get a lot of other information at that place.
How to protect computers from MDS?
Near all operating systems take issued a patch which should be used in addition to the Intel microcode to proceed the vulnerability away. On Windows OS, the Tuesday updates are said to have patched most computers. This, along with the Intel code that is existence congenital into the operating system patches, should be sufficient to prevent microarchitectural sampling (MDS) from compromising your computers.
MDSAttacks website recommends disabling Simultaneous Multi-Threading (SMT), also known every bit Intel Hyper-Threading Engineering science, which significantly reduces the bear on of MDS-based attacks without the cost of more than complex mitigations. Intel has also provided CPU microcode updates, and recommendations for mitigation strategies for operating system (and hypervisor) software. Nosotros recommend you install the software updates provided past your operating system and/or hypervisor vendor.
Proceed your computer(due south) updated. Update your BIOS and download the latest device commuter for your processor from the Intel website.
This vulnerability has been patched by Microsoft for their Windows line of operating systems. macOS too received a patch on May 15th, 2019. Linux has prepared the patches just needs to be downloaded separately for Microarchitecture Data Sampling (MDS).

Source: https://www.thewindowsclub.com/microarchitectural-data-sampling-mds-vulnerability
Posted by: gladneysatond1937.blogspot.com


0 Response to "Microarchitectural Data Sampling (MDS) vulnerability explained"
Post a Comment